When we began preparing our organization for ISO 27001 certification, we made one thing clear — we didn’t want to do it just to earn a certificate.
As a company building healthcare solutions, including our flagship platform Zymez Health, we knew that data security isn’t a checklist — it’s a culture. Every patient record, every API call, and every log file carries a responsibility — to protect trust.
After onboarding our first set of healthcare customers, we started strengthening our platform’s security posture. That’s when we discovered Wazuh, an open-source security platform that didn’t just help us prepare for compliance — it helped us establish a security cadence across our organization.
With Wazuh, we began to see security not as a one-time activity but as a living, breathing process — continuous, visible, and shared across the team.
Building Security into Our Workflow — Image Scanning with Wazuh and Trivy
Once Wazuh was up and running, we began integrating it into the daily rhythm of our development and deployment processes.
The first area we focused on was something that affects every modern platform — container security.
Our Zymez Health platform runs as a set of microservices packaged in Docker containers, and like any engineering team, we continuously build, update, and deploy these images. But as the platform scaled, we needed a consistent, automated way to ensure that no image with known vulnerabilities ever reached production.
That’s where Trivy came in.
Trivy is an open-source vulnerability scanner that inspects Docker images for known CVEs (Common Vulnerabilities and Exposures).
We integrated Trivy into our Bitbucket CI/CD pipelines, so every time a new Docker image was built, the following would happen automatically:
Trivy scans the freshly built image for OS and library-level vulnerabilities.
The scan results are forwarded directly to Wazuh using its built-in vulnerability management module.
Wazuh aggregates the results in its dashboard — showing severity levels, affected components, and recommended fixes.
Our team gets notified in real time, enabling developers to fix vulnerabilities before deployment.
This integration gave us two powerful outcomes:
Continuous visibility — every image that moves through our pipeline is automatically assessed.
Actionable insight — we can correlate vulnerabilities across containers, servers, and applications — all in one Wazuh dashboard.
For us, this was a turning point.
Security wasn’t just a step before release anymore — it became a continuous part of our build process.
“If code moves fast, security should move with it — not chase it.”
Securing Our Cloud Assets — Visibility That Drove Real Change
The next step in our security journey was to bring our cloud infrastructure under continuous monitoring.
Since our deployments run on DigitalOcean VMs, we installed Wazuh agents on each cloud asset to track activity, configuration changes, and vulnerabilities in real time.
Almost immediately, Wazuh began surfacing data that we’d never seen so clearly before.
The biggest eye-opener?
The sheer number of brute-force login attempts targeting our public-facing servers.
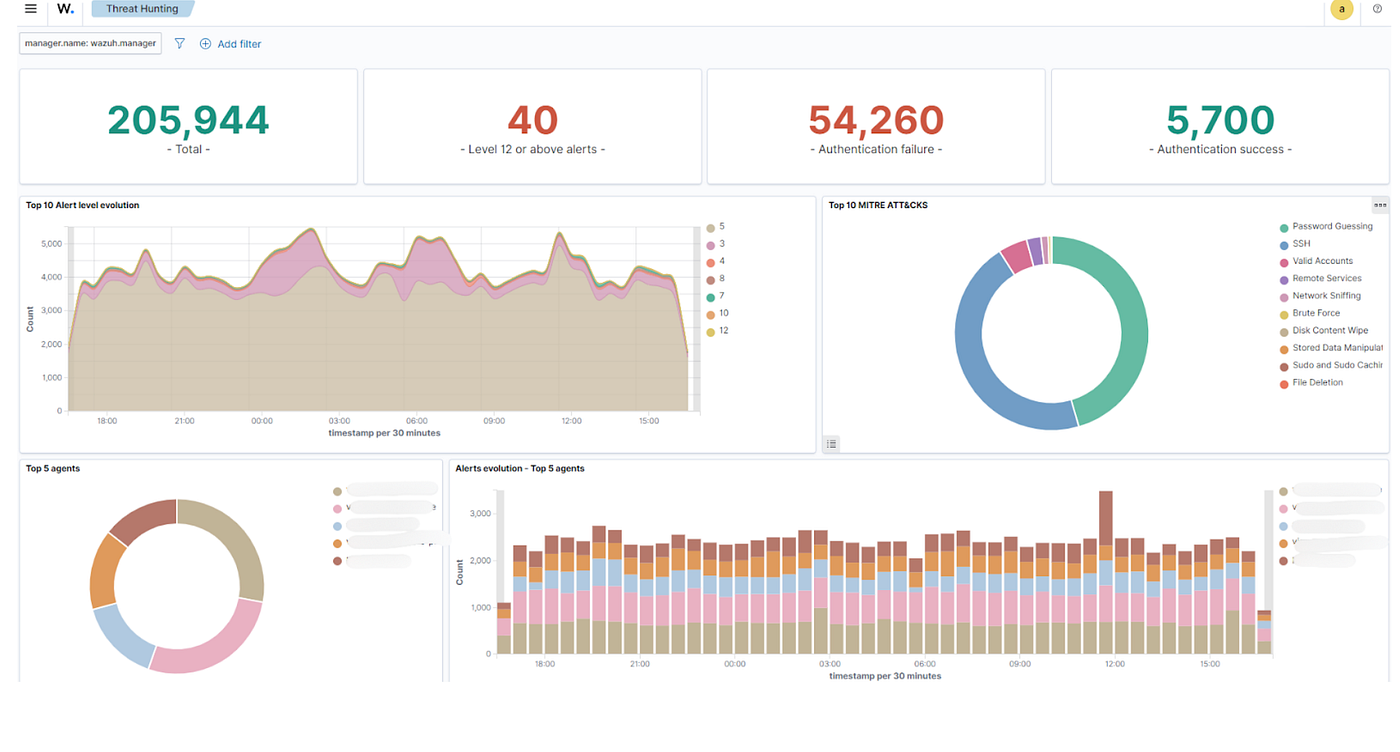
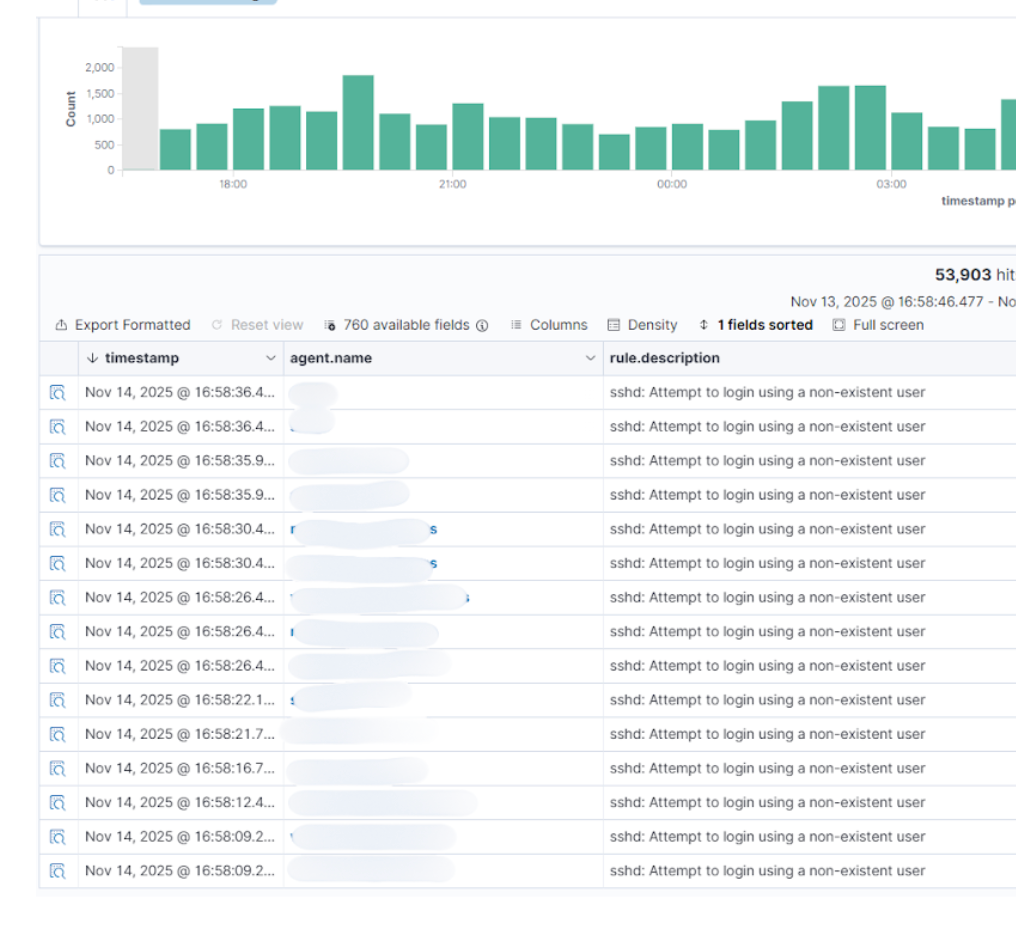
Within days, we implemented a major improvement:
- Disabled all password-based SSH logins.
- Switched entirely to SSL certificate–based authentication for authorized users only.
- Reduced external attack surface by tightening firewall rules based on Wazuh’s log analytics.
Wazuh also started helping us in patch management.
Its built-in vulnerability detection module monitored the OS patch levels and highlighted the top 5 most vulnerable packages on each server.
This allowed our DevOps team to act proactively — applying updates before they could become exploitable risks.
That single change — moving from reactive patching to data-driven updates — drastically improved our security hygiene and team confidence.
Wazuh didn’t just show us alerts — it showed us what to fix, and why.
Hardening Our Cloud Environments — The Power of Security Configuration Assessment (SCA)
Once our vulnerability and asset monitoring were in place, we turned our attention to configuration security — the often-overlooked layer that determines how resilient your infrastructure truly is.
Even a fully patched system can be vulnerable if it’s misconfigured — weak permissions, unused services left open, default SSH settings, or unprotected logs.
That’s where Wazuh’s Security Configuration Assessment (SCA) module made a major impact.
We enabled SCA across all our DigitalOcean VMs, allowing Wazuh to automatically benchmark our servers against industry-standard hardening baselines such as:
- CIS (Center for Internet Security) benchmarks,
- ISO 27001 control mappings, and
- Common Linux security best practices.
Almost immediately, the reports surfaced several OS-level misconfigurations that had quietly slipped through over time:
- Services running that were no longer required.
- Files or directories with overly permissive access rights.
- Logging configurations that weren’t retaining enough historical data.
- SSH settings that still allowed certain legacy ciphers.
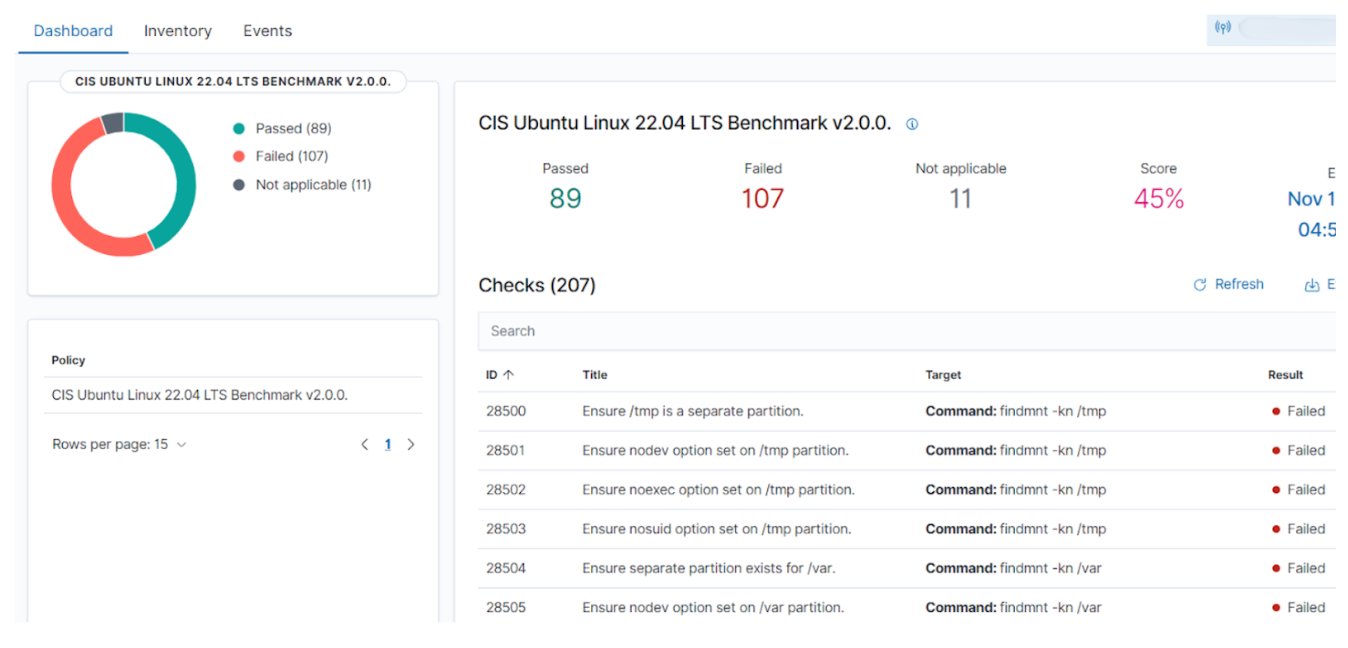
Each of these findings came with clear remediation guidance, helping our DevOps team harden the environment step-by-step — directly from the Wazuh dashboard.
The results were tangible:
- Reduced our overall SCA risk score by more than half within weeks.
- Brought our infrastructure in line with ISO 27001 Annex A controls for configuration management.
- Established a baseline for continuous compliance, where new assets automatically inherit the same hardened configuration templates.
What stood out most was how easy it was to operationalize — no complex integrations or new agents required.
Wazuh simply became our baseline guardian, constantly reminding us that good security isn’t just about patching — it’s about posture.
“Patching fixes known issues. Hardening prevents the next ones.”
Detecting the Unexpected — Malware Detection and File Integrity Monitoring
Even with vulnerability scanning and configuration hardening in place, security is never static.
In live environments — especially those running web-facing applications — threats can still slip through.
That’s where Wazuh’s Malware Detection and File Integrity Monitoring (FIM) modules became invaluable.
We configured FIM across our critical infrastructure — particularly for:
- Web application directories,
- Database configuration files, and
- Key system binaries on our DigitalOcean VMs.
Wazuh continuously monitors these locations for any unauthorized changes, additions, or deletions, and raises alerts when anomalies occur.
It didn’t take long before this setup proved its worth.
During one of our regular Wazuh dashboard reviews, we noticed an unusual file modification alert on one of our WordPress deployments.
The affected file wasn’t part of any recent code update — and the hash didn’t match our known baseline.
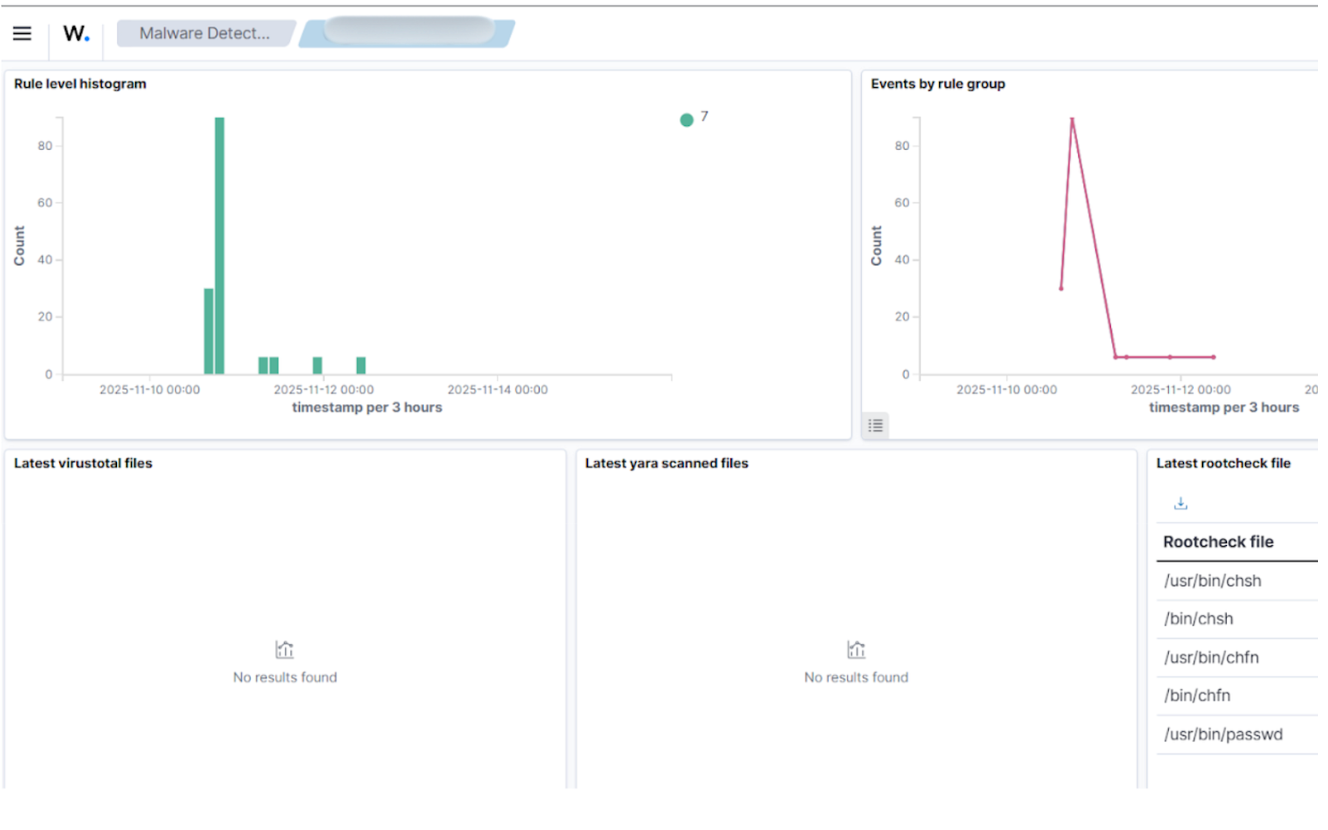
On deeper inspection, we discovered a malicious script injected into one of the theme files — classic malware behavior.
Thanks to the early alert from Wazuh’s FIM and malware detection engine, we were able to:
- Immediately quarantine and remove the infected file.
- Verify system integrity across the remaining WordPress installations.
- Tighten security on uploads, plugins, and permissions to prevent recurrence.
That single incident validated the purpose of our entire monitoring setup.
It demonstrated how Wazuh helps not just in compliance or visibility — but in real-time detection and swift response.
Wazuh didn’t just tell us something was wrong — it helped us act before it became worse.
Security as a Continuous Activity
Our journey with Wazuh so far, has transformed the way we approach security — from a one-time compliance activity to a living, evolving practice.
As a company building AI-driven healthcare solutions, security isn’t just a requirement — it’s a core part of our promise to our clients. By implementing Wazuh, we’ve been able to take a proactive approach to monitoring, identifying vulnerabilities, detecting anomalies, and continuously improving our security posture.
Wazuh has made it easy to have real-time visibility into our security landscape. With everything in one place — from malware detection to file integrity to vulnerability scanning — we can act quickly when needed and stay ahead of emerging threats.
But this is just the beginning.
As we continue to grow and scale, we are now focusing on extending Wazuh’s monitoring capabilities to our development assets. We want to ensure that our dev environments are as secure as our production systems, closing any gaps early in the CI/CD pipeline.
We’re also exploring how Wazuh can help us audit our compliance with industry standards like HIPAA and GDPR. (which I will cover in a separate article)
The ability to automatically assess compliance and provide real-time audit-ready reports is not just a huge time-saver, but an enabler of trust for our customers in healthcare.
It’s exciting to think about how Wazuh will continue to evolve alongside our platform, supporting security, privacy, and compliance as we scale.
Security isn’t just about being compliant — it’s about being ready. Ready to detect, ready to respond, and most importantly, ready to keep improving.








